Ghost CMS has introduced two-factor authentication (2FA) to boost security for staff logins by requiring email verification codes, especially on new devices. While this enhances protection, it caused issues for local development setups where emails couldn’t be sent, locking out developers. This article explains the update and provides a clear fix: configuring Ghost to send emails via Gmail using a Google App Password. Step-by-step instructions guide developers through setting up SMTP settings in their config file, so they can resume working smoothly while benefiting from Ghost's improved security.
2FA Security Update by Ghost CMS
Ghost CMS has rolled out a significant security update: two-factor authentication (2FA) for staff user logins. This change introduces device verification and optional email-based 2FA as extra layers of protection for Ghost administrators.
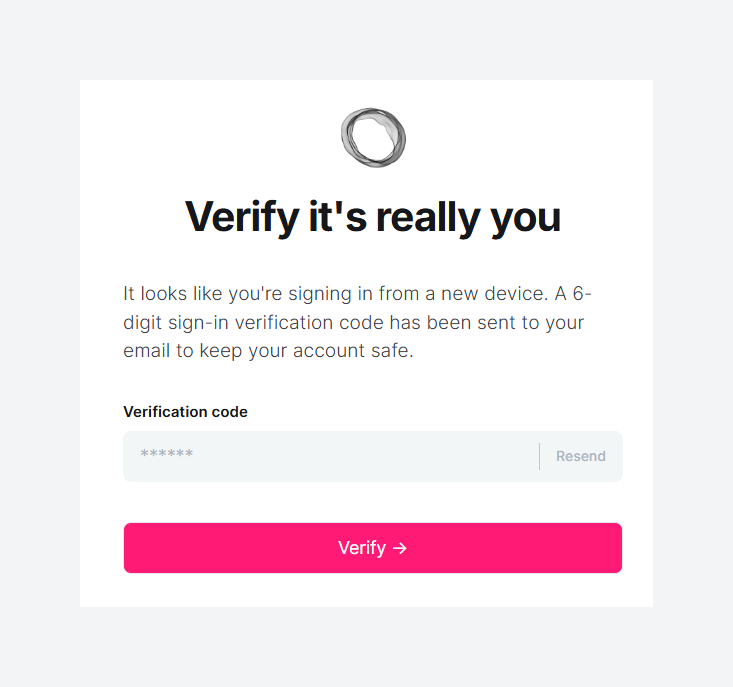
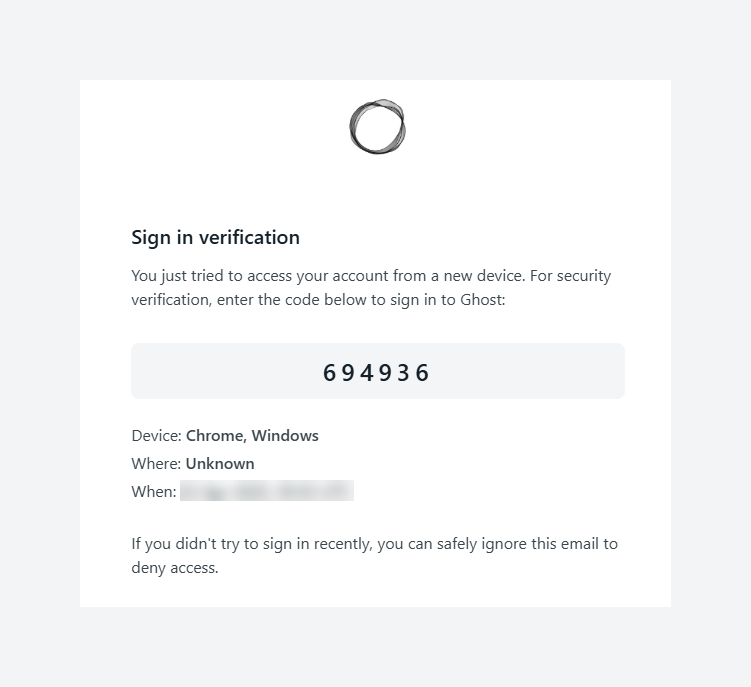
In practical terms, when a user signs in from a new or unrecognized device, Ghost will now email them a six-digit verification code that must be entered to complete the login. Site owners can even choose to require these email 2FA codes for all staff logins.
It’s a welcome enhancement that makes it much harder for unauthorized parties to access a Ghost publication’s admin area, even if a password is compromised.
Ghost CMS now includes a “2FA confirmation” prompt when the staff user logs in from a new device. This screen asks the user to enter a 6-digit verification code sent to their registered email address. It provides an extra layer of protection to ensure that even if a password is stolen, an attacker cannot log in without also having access to the user’s email.
This move is part of Ghost’s broader focus on security best practices. Ghost’s development team emphasizes building a secure platform by employing modern safeguards and welcoming external security reviews.
Out of the box, Ghost already implements measures like brute-force login protection (limiting login attempts to 5 per hour per IP), automatic SSL setup via Let’s Encrypt, and strong password hashing with bcrypt. Adding 2FA for staff logins fits right into this security-conscious philosophy, giving users and administrators greater peace of mind.
The Developer’s Dilemma: 2FA Emails in Local Development
While the new 2FA feature is great for security, it did introduce an unexpected hiccup for developers working on Ghost locally.
If you run a self-hosted Ghost instance on your local machine (for theme development or testing, for example), you might suddenly find that logging into your local Ghost Admin now triggers a 2FA email.
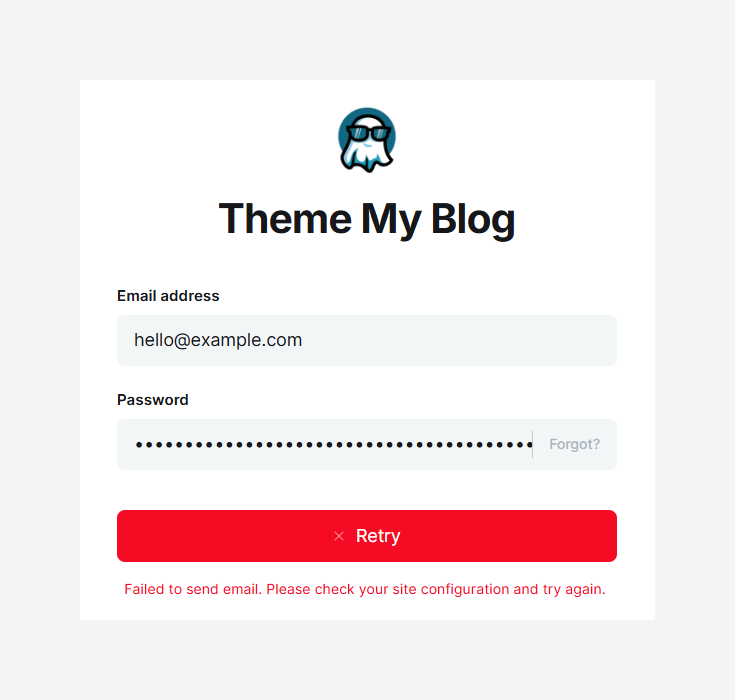
Ghost will attempt to send a one-time code to the email address of your admin user – which, in a development environment, often isn’t set up to actually send emails. The result? You get stuck at the login screen without a code, interrupting your development workflow.
My local Ghost install recently started trying to email 2FA login codes, so I configured it to send those emails via Gmail using an app password. In essence, the solution is to configure Ghost’s mail settings in the local development config file.
By setting up an SMTP service (like Gmail or any other email provider), your local Ghost can successfully deliver the 2FA tokens to you, allowing you to log in and continue working. Fortunately, it’s pretty easy to set up. Let’s walk through the fix step-by-step.
How to Fix Ghost 2FA Email Issues in Development (Step-by-Step)
To avoid getting locked out by 2FA on your local Ghost site, you’ll need to set up an SMTP email configuration. Here’s how to do it:
1. Generate a Google App Password
If you want to use a Gmail account to send Ghost’s emails, you’ll need a Google App Password (a special 16-digit passcode for third-party apps).
Then, log in to your Google Account settings and navigate to Security → App Passwords (this option is difficult to find, at least for me, so use the direct link).
Create a new app password for Ghost (you can label it e.g. "Ghost Dev").
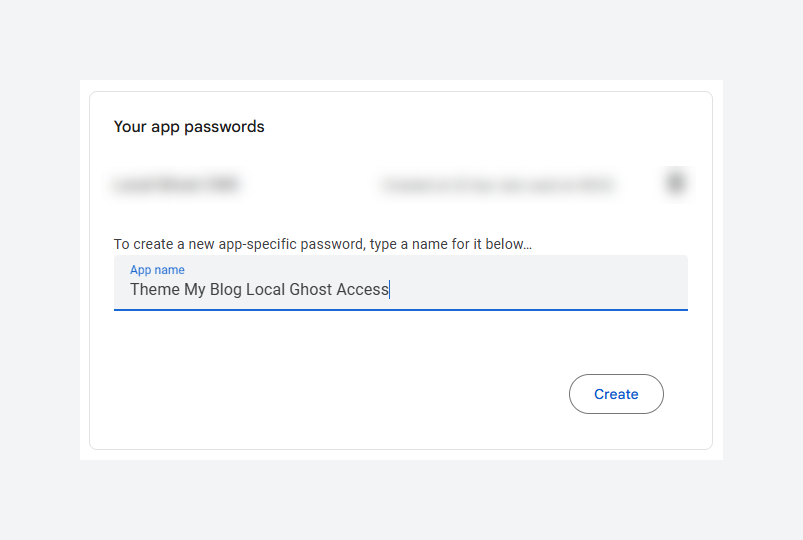
Google will then display a 16-character password – copy this code and store it somewhere safe (you’ll need to paste it into Ghost’s config next).
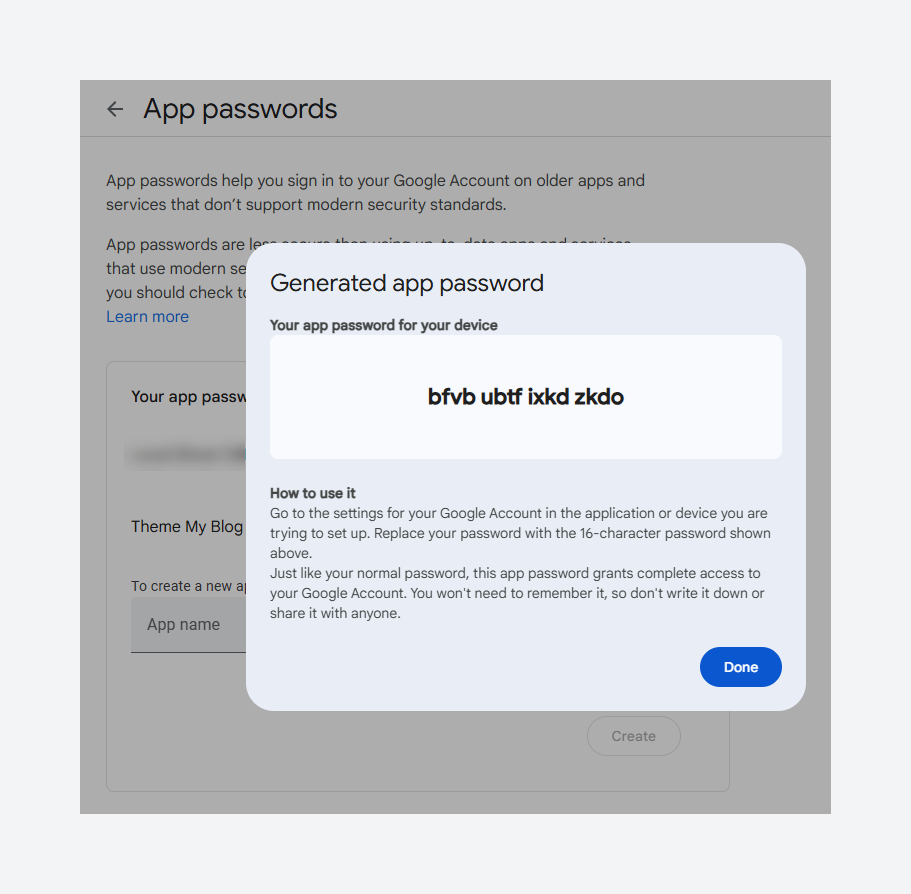
2. Add the App Password to Ghost’s config file
Next, open your Ghost configuration file for your development environment. If you’re running Ghost locally in development mode, this is likely the config.development.json file in your Ghost installation directory.
In that file, find or add a "mail" setting that defines your SMTP details. For Gmail, it will look something like this:
{
"mail": {
"from": "[email protected]",
"transport": "SMTP",
"options": {
"service": "Gmail",
"host": "smtp.gmail.com",
"port": 587,
"auth": {
"user": "[email protected]",
"pass": "bfvb ubtf ixkd zkdo"
}
}
}
}In the above, replace "[email protected]" with the Gmail address you’re using, and add your application password in the "pass" field (line #11) with the 16-character app password you obtained in Step 1. The "from" address can be the same Gmail address.
This configuration tells Ghost to use Gmail’s SMTP server with your credentials. Save the changes to the config file.
3. Restart Ghost and log in with 2FA
After updating the config, restart your local Ghost instance so it picks up the new mail settings.
If you’re using the Ghost CLI, you can run ghost restart . Now, try logging into your Ghost admin again. This time, when Ghost needs to send a 2FA code, it will use the SMTP settings you provided.
Check your Gmail inbox for the verification code email (it may show up in Spam if not in Inbox). Enter the code from the email into the Ghost 2FA prompt, and you should be logged in successfully. 🎉
At this point, your development workflow should be back to normal – with the added benefit of Ghost’s new security measures fully operational. Once the initial device verification is done, Ghost will remember your device, so you likely won’t be asked for another code on every login. And if you do get prompted again, the email configuration will handle it seamlessly.
In summary, Ghost’s new 2FA feature brings stronger security to the platform, and with a quick one-time email setup, even local developers can enjoy this security without any disruption. It’s great to see Ghost evolving its security features, and now you can develop on Ghost knowing your admin access is both safe and convenient. Happy coding, and stay secure! 🛡️✨